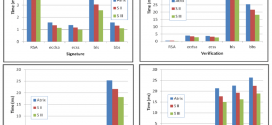
برخی از معروفترین روشهای شکستن کد ها عبارتند از:
Frequency Analysis
Algorithm Errors
Brute Force Attacks
Human Error
Social Engineering
حملات در رمزنگاری:
Attacking the key
Attacking the Algorithm
Intercepting the Transmission
Birthday Attack
Weak key Attack
Mathematical Attack
چهار نوع عمومی از حملههای رمزنگاری
- حمله فقط متن رمز شده Only – text attack
- حمله متن معلوم Known – text attack
- حمله متن منتخب Chosen – text attack
- حمله تطبیقی متن منتخب Adaptive chosen text attack
توضیحات تکمیلی:
These are some examples of ‘active attacks’:
- Bruteforce attacks
Brute-force attacks involve trying every possible character combination to find the ‘key’ to decrypt an encrypted message. While brute-force attacks may take a smaller amount of time for smaller keyspaces, it will take an immeasurable amount of time for larger keyspaces. Hence it is impractical to try brute-force attacks modern encryption systems.
- Cipher-only attack
In the ‘cipher-only’ attack, the attacker knows the ciphertext of various messages which have been encrypted using the same encryption algorithm. The attacker’s challenge is to figure the ‘key’ which can then be used to decrypt all messages.
The ‘cipher-only’ attack is probably one of the easiest attacks to commit since it is easy to capture the ciphertext (by sniffing) but difficult to implement since the knowledge about the encryption process is limited.
- Known-plaintext attack
In the ‘known-plaintext’ attack, the attacker knows some of the plaintext and the ciphertext. He then has to figure the ‘key’ by reverse engineering and he can decipher other messages which use the same ‘key’ and algorithm.
The ‘known-plaintext’ attack was effective against simple ciphers such as the ‘substitution cipher’. It was popular for breaking ciphers used during the Second World War.
- Chosen plaintext attack
The ‘chosen-plaintext’ attack is similar to the ‘known-plaintext’ attack, but here the attacker experiments by choosing his own plaintext (say choosing a word such as ‘cryptography’) for a ‘Vignere cipher’ and with the generated ciphertext he can figure the ‘key’.
Once he figures the ‘key’ he can learn more about the whole encryption process and understand how the ‘key’ is being used.
With this information, he can decrypt other messages.
- Chosen ciphertext attack
In the ‘chosen ciphertext’ attack, the attacker chooses a portion of the decrypted ciphertext. He then compares the decrypted ciphertext with the plaintext and figures out the key.
This is relatively a harder type of attack and earlier versions of RSA were subject to these types of attacks.
- Differential cryptanalysis
This was a popular type of attack against block algorithms such as DES in 1990. The primary aim of this attack, as with other attacks, is finding the ‘key’.
The attacker follows several messages of plaintext into their transformed ciphertext. He observes the changes form plaintext to the ciphertext and deduces the key.
This is a type of ‘chosen-plaintext’ attack since the attacker chooses the plaintext to observe the transformation.
- Linear cryptanalysis
The attacker carries out a “known-plaintext” attack against several messages which have been encrypted with the same key. This gives the attacker insight into the probability of a particular key. If more messages are attacked, there is a higher possibility of finding the particular “key”.
- Side channel attacks
Apart from just relying on mathematical ways to break into systems, attackers may use other techniques such as observing power consumption, radiation emissions and time for data processing. With this data, the attacker works in a reverse manner to figure the ‘keys’ to an algorithm just by observing the amount of heat released in an attack.
RSA keys in 1995 were uncovered using this type of attack.
- Replay attacks
In a ‘replay attack’, the attacker captures some information (as an example, authentication information) and re-submits it back to the receiver. This dupes the receiver and they give the attacker unauthorized access.
Timestamps are one of the important countermeasures to handle ‘replay attacks’.
This post outlined the basic concepts of cryptography and some of the popular cryptography attacks.
- Attacks Against Encryption Systems. The most famous attacks against encryption systems includes, but may not be limited to the following:
- Evil Maid Attack. …
- Bootkit and Rootkit Attacks. …
- Cold Boot Attack. …
- Brute-Force Sign-In Attacks. …
- Direct Memory Access. …
- Encrypting Ransomware Attacks. …
- Countermeasures Against Encryption Attacks.
سه تا مطلب عالی در مورد این موضوع:
 تعاونی نیرومندسازی تحقیقات جامع ترین مرجع دانلود تحقیق، مقاله، سمینار و پایان نامه
تعاونی نیرومندسازی تحقیقات جامع ترین مرجع دانلود تحقیق، مقاله، سمینار و پایان نامه